How Remote Spy Software works
Remote install and remote monitoring overview
RemoteSpy is the industry leader in remote install spy software solutions. Remote Spy's innovative features include anti-detection routines and firewall bypassing options to insure a successful computer monitoring investigation. RemoteSpy is widely used by employers, parents, and private investigators around the world to monitor their own computers or the computers of their clients. Optionally remotely install with confidence without worrying about IP addresses or having to directly connect to your remote computer. Know with certainty what they are doing on your computer while you are away.
Step 1: Purchase RemoteSpy
Before purchasing Remote Spy you must first acknowledge and agree that you are the owner of the remote computer you desire to install the spy software onto OR that you have proper written consent from the computer owner. This is of the utmost importance, and failure to do so can result in being investigated by the FTC or charged with criminal conduct by state or federal authorities. We DO NOT condone, tolerate or promote the use of our software for illegal purposes.
If you qualify and are ready to purchase, please visit the Purchase Remote Spy page and fill in the required information to place your spy software order.
Step 2: Create RemoteSpy.com account
After your purchase has been completed you will be sent an Order-ID via email. Your Order-ID is required for Registering your RemoteSpy account. The registration process will ask for your Order-ID, Name, E-mail Address, and your choice of Username and Password. All information provided is kept confidential and will never be sold to third parties.
Step 3: Build RemoteSpy Module
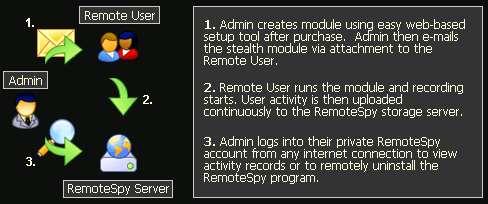
RemoteSpy features a unique web-based configuration tool for creating your personal RemoteSpy Software Module from any Internet enabled computer (Windows, MAC or Linux). This allows you to only download a single file that is pre-configured with your chosen settings and ready for deployment at your discretion! Other software solutions require you to download cumbersome installation utilities. Remote Spy's web-based creator saves you valuable time, and always provides you with convenient access to the latest version of RemoteSpy. An installation utility version is available upon request or for those that order a CD.
Step 4: Deploy RemoteSpy Module
Once you have created your RemoteSpy module and downloaded it, you can then begin deployment. To install remotely you can attach the RemoteSpy module exe file to any regular email and then send to the remote computer (that you must own or have permission to monitor). To install, the remote user of your computer only has to open the module and accept the monitoring software installation notice. It is NOT our responsibility to get the user to execute the module. Another popular method of remote deployment is instant messenger file sending. Alternatively you can directly install the software physically by opening the module from the web-based creator, deploying from a cd, floppy disk, or usb storage device - all of which will provide instant results.
We have received a LOT of email from parents and employers who want to install the module on their child's or employee's PC which they own, but do not have physical access to that PC in order to install the module. Obviously, there are times when you don't want your child or employee to know you are monitoring them, but so long as the computer being monitored is owned by you (or you have written consent of the computer's owner), then you have the right to install any software you want onto that computer. If you do not own the computer being monitored or do not have written permission to monitor it, then you simply cannot use RemoteSpy. Such an unauthorized use would be a violation of the license agreement and, very possibly, against the law.
Step 5: Login and View RemoteSpy Logs
After the user runs the file, their activities will be stored on our servers, so that you can login at your convenience and securely view them from any internet connection with a web-browser. Logs are updated every 10 minutes as long as the remote computer is turned on and is connected to the internet.

|

